Before we start with this topic I would like to explain the existing methodologies used to prevent spoofing and phishing, these two together cause a great threat to almost all organizations around the world. Most of us knows SPF records are considered critical and highly recommended to prevent any spoofing and phishing attack in the name of your organization, however there are many organizations which have not enabled SPF lookup for inbound mails to validate if the mail came from a legitimate source. With time passing DMAC and DKIM are the new two features introduced to validate the authenticity of the sender. Let us try to understand how each of these work and later move on to implementing DKIM same in Office 365.
How an SPF record works?
SPF uses a DNS TXT record to provide a list of authorized sending IP addresses for a given domain. Those companies with mail servers which are enabled to do a SPF lookup for all received mails will validate the authenticity of the sender by doing a reverselookup for spf record of sender domain. Here, the receiving server will look at the email header for “Mail From” portion extract the domain from name here and validate the SPF record published for this domain. In the below example, fabrikam.com domain is extracted and spf reverselookup is done for fabrikam.com. If the sending server IP and IP of servers mentioned in the SPF record matches the mail is allowed in to the organization else the mail is rejected. When we enable strict SPF lookup in the receiving side, mails from organization who doesnt have a spf record published will be straight away rejected.
Example Header:
Mail from: Josh@fabrikam.com
Rcpt to: astobes@contoso.com
How a DKIM works and what are the extensive security over SPF?
“Domain Keys Identified Mail” is an advanced security feature which is used along with SPF to prevent spoofing and phishing attack on the domains. When DKIM is enabled for your domain, all emails sent out from the server will be digitally signed using cryptographic authentication. Receiving server can use this digital signature to determine if the email is legitimate. DKIM uses a private key to encrypt the header of all outgoing mail. Receiving server will look for the DKIM public key (published in the DNS) of the sending domain to decode the signature. If the mail is coming from an unauthorized server, the signature can’t be decoded there by preventing any spoofing attempt.
We can say SPF and DKIM together provides a greater protection from Spoofing attack. Consider two domains spoofing.com and genuine.com hosted in same cloud multitenant infrastructure. Now, spoofing.com user is sending out spoofing message as user@genuine.com to user@recepient.com. SPF records for both the domains spoofing.com and genuine.com will be same in this case so there is a chance that recipient.com will accept the mail after validating the SPF record. Considering DKIM implemented along with SPF, recipient.com will try to decrypt the signature of genuine.com using the public key published using DNS. If decrypted mail is allowed in to the organization else rejected.
How DMARC works? Advantages of DMARC over SPF.
To understand DMARC, we should understand below two headers.
- a) “Mail From” address Identifies the sender and specifies where to send return notices if any problems occur with the delivery of the message, such as non-delivery notices. This is sometimes called the 5321.MailFrom address or the reverse-path address. SPF records are checked against the domain in this header.
- b) “From” address is the address displayed in outlook, “From” Address is not authenticated with SPF. In short, user can still get a spoofed mail which had passed SPF against “Mail From” address. DMARC records are verified against domain of this header.
DMARC works the same way as SPF, here the DMARC TXT records will have the details of the authorized sending servers. As soon as a mail is received by the receiver server “FROM” header is stripped and the sending domain servers are validated against DMARC records. If the sending servers are not the authorized servers, mail is dropped.
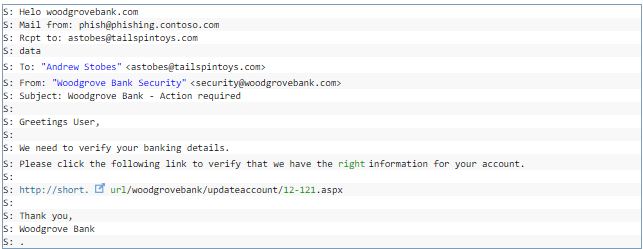
Advantage of DMARC over SPF,
In the below example, “Mail from” and “From” headers are different. Here SPF is validated against “Mail from” header, so even if the sender had spoofed the “From” header the mail will be rejected post validating against DMARC records.